Using NEOSYS Generally: Difference between revisions
mNo edit summary |
mNo edit summary |
||
| (120 intermediate revisions by 10 users not shown) | |||
| Line 1: | Line 1: | ||
== | == Getting started with NEOSYS == | ||
#Reset your browser to factory settings to ensure all 3rd party toolbars/pop-up blockers are removed and browser cache is cleared. See [[Reset Browser]] for instructions. | |||
#Reopen the browser and ensure that the pop-up blocker is disabled. See [[Disabling Popup Blocker]] for instructions. | |||
#Enter the NEOSYS URL. | |||
#Add this URL to your favourites. | |||
#You should now see the Login page. If you are a new user or have forgotten your password click on [[How to reset the password?]] for instructions on how to get your password | |||
#Enter your Username, Password, select the database and click on login. See http://youtu.be/dS62_eSCm-A to learn how to login to NEOSYS. | |||
#You should now see the user details page. | |||
== Using the NEOSYS testing and training database == | |||
Standard NEOSYS practice is to setup a "testing and training" database for each operationally live database. This testing and training database is very useful to try out procedures in NEOSYS without having any real live or permanent effect. The testing and training database is virtually a copy of the live data because every night the live database is cloned over (copied) to the test database. This database is generally available to everybody who has access to the live database unless specifically restricted. | |||
*To access the test database, first log out of the live database if you are logged in, then chose the test database from the dropdown on the login screen before logging in. | |||
*Since the test database is a copy of the live database as at last night (around 1am) it contains up to date info for you to play with any time you like. | |||
*Any work you do in the test database has no effect whatever in your live database. | |||
*There is no way to copy any work done in the test database to the live database | |||
*Since any testing work done in the test database will be OVERWRITTEN during the night, if you wish to perform extended testing which extends overnight, you can ask NEOSYS support to suspend the nightly copy. | |||
*Passwords in the test database are a COPY of whatever was in the live database at the time it was copied (usually last night). Resetting the password in LIVE or TEST does not affect the other database. | |||
*Documents and reports generated from the test database have a mark (in red) in the heading to indicate that they did not come from the live system. This helps to reduce confusion in case people lose track of which system they are working in. | |||
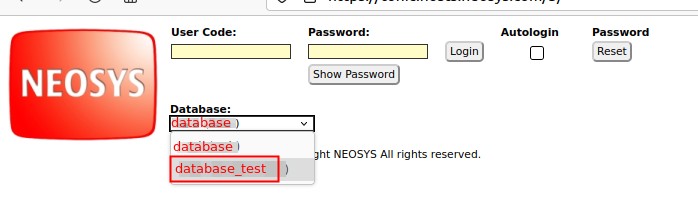
<BR>'''Screen logging in to test database:''' | |||
[[File:Logintest.jpg]] | |||
<BR>'''Document showing red warning in heading:''' | |||
[[File:Docredwiki.jpg]] | |||
== Restricting user access to files == | |||
=== Restricting user’s access to certain records of a file depending on company/division === | === Restricting user’s access to certain records of a file depending on company/division === | ||
| Line 43: | Line 73: | ||
Due to limitations in the size of the authorisation file, this should be limited to no more than a few 10’s of records in total for all files. | Due to limitations in the size of the authorisation file, this should be limited to no more than a few 10’s of records in total for all files. | ||
== Codes in NEOSYS == | == Codes in NEOSYS == | ||
| Line 192: | Line 112: | ||
IBM - IBM Corporation (rule 1: Standard abbreviation although in practice would probably have a geographical location appended) | IBM - IBM Corporation (rule 1: Standard abbreviation although in practice would probably have a geographical location appended) | ||
STBU - Stephen | STBU - Stephen Burns (rule 3: Personal names code well in using four letters) | ||
STBU2 - Stephan Butros (Rule 4: An accidental duplication .. simply add 2) | STBU2 - Stephan Butros (Rule 4: An accidental duplication .. simply add 2) | ||
| Line 200: | Line 120: | ||
GIOIJE - Gulf Oil Jeddah (Rule 5:) | GIOIJE - Gulf Oil Jeddah (Rule 5:) | ||
== | == What is NEOSYS password policy? == | ||
NEOSYS automatically generates short, memorable passwords for users and sends them to their registered corporate email address. Users can request their initial password, or a new password, at any time as long as their account is valid. | |||
A NEOSYS automatically generated password is a four letter "word" in the pattern "CVCV" - consonant, vowel, consonant, vowel. These are short and memorable like "KILA". This reduces the occurrence of users noting down their passwords in insecure locations and therefore tends to increase overall security. Also, since users cannot pick their own passwords, weak passwords are avoided thereby tending to increase overall security. | |||
Three failures to login, for whatever reason, causes a user account to become locked until a new password is requested. Automatic lockout makes password guessing attacks infeasible despite the shortness of the NEOSYS password. Users can unlock their own account by simply requesting a new password. | |||
When a login is refused, no specific reason is given, only a message that lists all the possible reasons for login failures. Either the username or password is incorrect or the account has been locked and a password reset should be done. Not being told the specific reason for failure to login is rather unhelpful for legitimate users but it is considered to be a standard security practice to avoid providing any information that might facilitate unauthorised access attempts. | |||
Users can update their own email address, but only after logging in successfully, and only to the companies corporate email servers. The email address part after the @ sign is restricted. This prevents password resets being sent to third party email systems which are outside the control of the company (like gmail.com etc.) unless specifically allowed. | |||
=== Forcing users to change password regularly === | |||
The | Enforcing periodic change of user passwords is an optional policy set per database in NEOSYS. The maximum number of days between password changes can be set and applies to all users. If a user does not change their password within the maximum period then their account is locked and they cannot login until they request a new password in the usual way from the login screen. | ||
Enforcing periodic change of user password is often considered an essential component (but only a component) of overall computer security. The concept is that people who improperly gain, or retain, access to the system, but do not have access to corporate email and therefore are unable to avoid password expiry, will not have access permanently. | |||
For example: Someone leaves the company and a) has been been granted partial or unrestricted access to NEOSYS from outside the office and therefore continues to have physical access to NEOSYS despite having left the company and b) has not been removed or expired from the NEOSYS authorisation table due to administrative oversight. In this case, the person will *not* have permanent access to the system because they will not be able to renew their NEOSYS password because, having left the company, they no longer have access to their corporate email account. Note however that THEY WILL HAVE ACCESS although for a limited period of time. In the worst case, if they renew their password just before leaving, either by accident or design, they could have unauthorised access after leaving the company for a maximum period of the number of days specified for password renewal. | |||
Potential disadvantages of enforcing periodic password renewal: | |||
*May DECREASE security if it results in people writing down their password in insecure locations even though the passwords are memorable four letter word | |||
*Inconvenient for infrequent users like management - although management level access should really have greater security not less | |||
*Unpopular with users | |||
== Giving access to users using Authorisation file == | |||
Only NEOSYS Support are authorised to make changes to the Authorisation File. | |||
A designated person within the client company must approve of requests to make changes. | |||
Find more information: [http://userwiki.neosys.com/index.php/Authorisation_File Authorisation File] | |||
== Splitting single NEOSYS report columns like 1000.00USD into two columns in Excel == | |||
Many NEOSYS reports put currency amounts in a single column like 1000.00USD, ie as a single number followed by a currency code. It does this to keep reports compact and to provide multi-currency totals in a single column. | |||
In order to support pivot table or export into other systems it is sometimes necessary in spreadsheets like Excel to split the number and currency code into separate columns. | |||
In Excel, strangely there is no built-in way to split numbers from letters but the following steps will achieve the same or better. | |||
#Select the column that you want to split, and duplicate it to get two identical columns by inserting a column and copying the original column into it. | |||
#Remove the currency codes from the first column by selecting it and doing Edit, Find and Replace (Ctrl+H), select "Regular expressions" under "Other options". Search For [A-Z] and Replace With nothing. | |||
#Do the same on the 2nd column and Search for \d and Replace With nothing. | |||
=== | === Using Macros === | ||
These steps can trivially be recorded as a macro, maybe called Split Currency Amount, and re-performed on request on any future sheets. This makes splitting even easier than any built-in function. | |||
In order to record the macro, select the column then perform the steps, then stop recording and save the macro maybe as "Split Amounts". Assign a hot key like Ctrl+Shift+S to be able to repeat it easily in future. | |||
In order to redo the work on another column, select the column then replay the macro, or if you assigned a hot key, press that combination. | |||
== | == Showing signatures for people who are not users of NEOSYS == | ||
You can issue documents on behalf of anybody by typing in their name as the executive when creating the document, however this does provide a signature. | |||
Solution: | |||
#Create NEOSYS user to represent the “issuing” users. Email address: support@neosys.com. (Do not give password to client) | |||
#Upload signatures onto the User File for the issuing users. To update users other than yourself, you need to be authorised to do “USER UPDATE” | |||
#When creating documents on behalf of issuing users, enter the user code of the issuing user as the Executive. The default executive/issuing user can be setup per client and/or brand in the Client/Brand File if desired. | |||
== Using Google to search NEOSYS wikis == | |||
Mediawiki's built in search is nowhere near as smart as Google's but Googles search often lists non-NEOSYS pages. | |||
Search like this: | |||
neosys wiki "exchange rate" | |||
Putting Exchange Rate in "" quotes searches for the exact phrase instead anywhere either word appears | |||
Latest revision as of 11:21, 23 November 2023
Getting started with NEOSYS
- Reset your browser to factory settings to ensure all 3rd party toolbars/pop-up blockers are removed and browser cache is cleared. See Reset Browser for instructions.
- Reopen the browser and ensure that the pop-up blocker is disabled. See Disabling Popup Blocker for instructions.
- Enter the NEOSYS URL.
- Add this URL to your favourites.
- You should now see the Login page. If you are a new user or have forgotten your password click on How to reset the password? for instructions on how to get your password
- Enter your Username, Password, select the database and click on login. See http://youtu.be/dS62_eSCm-A to learn how to login to NEOSYS.
- You should now see the user details page.
Using the NEOSYS testing and training database
Standard NEOSYS practice is to setup a "testing and training" database for each operationally live database. This testing and training database is very useful to try out procedures in NEOSYS without having any real live or permanent effect. The testing and training database is virtually a copy of the live data because every night the live database is cloned over (copied) to the test database. This database is generally available to everybody who has access to the live database unless specifically restricted.
- To access the test database, first log out of the live database if you are logged in, then chose the test database from the dropdown on the login screen before logging in.
- Since the test database is a copy of the live database as at last night (around 1am) it contains up to date info for you to play with any time you like.
- Any work you do in the test database has no effect whatever in your live database.
- There is no way to copy any work done in the test database to the live database
- Since any testing work done in the test database will be OVERWRITTEN during the night, if you wish to perform extended testing which extends overnight, you can ask NEOSYS support to suspend the nightly copy.
- Passwords in the test database are a COPY of whatever was in the live database at the time it was copied (usually last night). Resetting the password in LIVE or TEST does not affect the other database.
- Documents and reports generated from the test database have a mark (in red) in the heading to indicate that they did not come from the live system. This helps to reduce confusion in case people lose track of which system they are working in.
Screen logging in to test database:
Document showing red warning in heading:
Restricting user access to files
Restricting user’s access to certain records of a file depending on company/division
In the following discussion remember that NEOSYS “companies” are used to implement any kind of corporate division. This includes legal entities and any type of internal division including departments, cost centres and profit centres etc.
Step 1 is to use the NEOSYS Authorisation File to generally restrict users access to certain companies/divisions, then they will also be restricted from viewing any records “belonging” to those companies/divisions. Split the groups in the authorisation file into multiple groups per division. For example, instead of one CLIENT SERVICE group in the Authorisation File you can create CLIENT SERVICE1, CLIENT SERVICE2 etc. The only difference must be a trailing integer so that the actual division name can be determined by NEOSYS.
For example to restrict access to company/division “XYZ” you create locked tasks in the NEOSYS Authorisation File as follows. The quotation marks are required.
COMPANY ACCESS “XYZ”
Invent a suitable lock eg =CFX to lock this company, place that lock on the newly created task and add that lock to the keys of the groups that should have access to that company.
Step 2 - Most of the various files in NEOSYS allow, and sometimes require, the association (i.e. tying) of individual records to specific companies/divisions either directly or indirectly.
Depending on the file, restrict access by entering one or more of the following on the individual records that are to be restricted.
- Company code
- A/c No. of an account which is tied to a specific company/division in its chart of accounts
- ”A/c No , company code” eg 99999,XYZ - in most places that you can enter the A/c No. you may also follow it with a comma then the company code.
- Codes of other records which are themselves tied to a specific company/division.
Important Note: brands are associated with the company of the account at the time that the brand was created and removing the company from the account code didnt free up the brand from the company which also includes removing the company code from the chart. Hence if you do such a change you need to run the following in maintenance mode:
F5 CREATEBRANDS Yes
Restricting access of users to specific individual records
Insert locked tasks in the Authorisation File similar to the following. For example, the following restricts access to company “XYZ”. The quotation marks are required.
COMPANY ACCESS “XYZ”
Generally, wherever there is a task called ‘filename ACCESS’ then you can add tasks like ‘filename ACCESS “XYZ” ’ to restrict access to individual records.
Other examples are:
ACCOUNT ACCESS “99999” MARKET ACCESS “INT”
Restricting access to the company and market files is rather special in that it also restricts access to any and all records associated with (ie “belonging” to or tied to) that company or market.
Due to limitations in the size of the authorisation file, this should be limited to no more than a few 10’s of records in total for all files.
Codes in NEOSYS
Inventing codes
In order to speed up data entry, NEOSYS usually allows codes to be entered directly instead of relying on name searches and popups which are slower.
There are three strategies to invent codes:
- Sequential numbers. Easy to generate codes for new records but the codes are difficult to remember and are meaningless
- Meaningful codes. Invent a pretty code so that when you look at the code it reminds you of the name. There are many alternatives though and it is usually difficult later on to re-guess/remember the exact code given only the name.
- Meaningless codes. Use some mechanical rule for generating a code from the name. If the rule is simple, then later on we can re-guess the code from the name easily. Unfortunately looking at the code usually does not remind us of the name.
The real aim of coding, if you think about it for a while, is to be able to know the code to enter it quickly even if all you know is the name. Therefore method three is the most useful.
Surprisingly, the main aim is NOT to know the name on seeing the code which is natural instinct of most people when coding. Meaningful codes are indeed pretty but usually it is difficult to remember the exact code for data entry.
Interestingly, it is common to find NEOSYS clients who have never met each other to be using identical codes for the same clients and suppliers etc.
Using Four letter coding system
This four letter coding system has proven over many years to be easy to use and surprisingly good at avoiding duplicate codes where there are thousands of records.
Follow these steps rigorously:
- If there is a well known abbreviation for something use that regardless of how many letters there are. e.g. IBM or UNESCO
- Remove all standard words from the name to be encoded. Egg The, Company, Al, Incorporated, Ltd etc
- If there is only one word left in the name take the first four letters otherwise take the first two letters of the first two words and ignore any following words.
- ACCIDENTAL DUPLICATIONS: If the code accidentally duplicates with another code, simply add a 2 or 3 or 4 onto the end of the code. DO NOT INVENT YOUR OWN CODES.
- PREDICTABLE DUPLICATIONS: If you know in advance that there are several similar accounts with almost the same name then first use the four letter rules rigorously ... and then add two letters e.g. country, town, currency etc to distinguish the duplicates.
Examples of four letter coding
NESO - NEOSYS Software Ltd. (rule 3: easy to take the first two letters of the first two words)
KHAL - Al Khaleej (rule 2 and 3: Remove the standard word Al and take the first four letters of the only word)
IBM - IBM Corporation (rule 1: Standard abbreviation although in practice would probably have a geographical location appended)
STBU - Stephen Burns (rule 3: Personal names code well in using four letters)
STBU2 - Stephan Butros (Rule 4: An accidental duplication .. simply add 2)
GUOIDU - Gulf Oil Dubai (Rule 5: We know there are many Gulf Oil records so we add two letters for the location)
GIOIJE - Gulf Oil Jeddah (Rule 5:)
What is NEOSYS password policy?
NEOSYS automatically generates short, memorable passwords for users and sends them to their registered corporate email address. Users can request their initial password, or a new password, at any time as long as their account is valid.
A NEOSYS automatically generated password is a four letter "word" in the pattern "CVCV" - consonant, vowel, consonant, vowel. These are short and memorable like "KILA". This reduces the occurrence of users noting down their passwords in insecure locations and therefore tends to increase overall security. Also, since users cannot pick their own passwords, weak passwords are avoided thereby tending to increase overall security.
Three failures to login, for whatever reason, causes a user account to become locked until a new password is requested. Automatic lockout makes password guessing attacks infeasible despite the shortness of the NEOSYS password. Users can unlock their own account by simply requesting a new password.
When a login is refused, no specific reason is given, only a message that lists all the possible reasons for login failures. Either the username or password is incorrect or the account has been locked and a password reset should be done. Not being told the specific reason for failure to login is rather unhelpful for legitimate users but it is considered to be a standard security practice to avoid providing any information that might facilitate unauthorised access attempts.
Users can update their own email address, but only after logging in successfully, and only to the companies corporate email servers. The email address part after the @ sign is restricted. This prevents password resets being sent to third party email systems which are outside the control of the company (like gmail.com etc.) unless specifically allowed.
Forcing users to change password regularly
Enforcing periodic change of user passwords is an optional policy set per database in NEOSYS. The maximum number of days between password changes can be set and applies to all users. If a user does not change their password within the maximum period then their account is locked and they cannot login until they request a new password in the usual way from the login screen.
Enforcing periodic change of user password is often considered an essential component (but only a component) of overall computer security. The concept is that people who improperly gain, or retain, access to the system, but do not have access to corporate email and therefore are unable to avoid password expiry, will not have access permanently.
For example: Someone leaves the company and a) has been been granted partial or unrestricted access to NEOSYS from outside the office and therefore continues to have physical access to NEOSYS despite having left the company and b) has not been removed or expired from the NEOSYS authorisation table due to administrative oversight. In this case, the person will *not* have permanent access to the system because they will not be able to renew their NEOSYS password because, having left the company, they no longer have access to their corporate email account. Note however that THEY WILL HAVE ACCESS although for a limited period of time. In the worst case, if they renew their password just before leaving, either by accident or design, they could have unauthorised access after leaving the company for a maximum period of the number of days specified for password renewal.
Potential disadvantages of enforcing periodic password renewal:
- May DECREASE security if it results in people writing down their password in insecure locations even though the passwords are memorable four letter word
- Inconvenient for infrequent users like management - although management level access should really have greater security not less
- Unpopular with users
Giving access to users using Authorisation file
Only NEOSYS Support are authorised to make changes to the Authorisation File.
A designated person within the client company must approve of requests to make changes.
Find more information: Authorisation File
Splitting single NEOSYS report columns like 1000.00USD into two columns in Excel
Many NEOSYS reports put currency amounts in a single column like 1000.00USD, ie as a single number followed by a currency code. It does this to keep reports compact and to provide multi-currency totals in a single column.
In order to support pivot table or export into other systems it is sometimes necessary in spreadsheets like Excel to split the number and currency code into separate columns.
In Excel, strangely there is no built-in way to split numbers from letters but the following steps will achieve the same or better.
- Select the column that you want to split, and duplicate it to get two identical columns by inserting a column and copying the original column into it.
- Remove the currency codes from the first column by selecting it and doing Edit, Find and Replace (Ctrl+H), select "Regular expressions" under "Other options". Search For [A-Z] and Replace With nothing.
- Do the same on the 2nd column and Search for \d and Replace With nothing.
Using Macros
These steps can trivially be recorded as a macro, maybe called Split Currency Amount, and re-performed on request on any future sheets. This makes splitting even easier than any built-in function.
In order to record the macro, select the column then perform the steps, then stop recording and save the macro maybe as "Split Amounts". Assign a hot key like Ctrl+Shift+S to be able to repeat it easily in future.
In order to redo the work on another column, select the column then replay the macro, or if you assigned a hot key, press that combination.
Showing signatures for people who are not users of NEOSYS
You can issue documents on behalf of anybody by typing in their name as the executive when creating the document, however this does provide a signature.
Solution:
- Create NEOSYS user to represent the “issuing” users. Email address: support@neosys.com. (Do not give password to client)
- Upload signatures onto the User File for the issuing users. To update users other than yourself, you need to be authorised to do “USER UPDATE”
- When creating documents on behalf of issuing users, enter the user code of the issuing user as the Executive. The default executive/issuing user can be setup per client and/or brand in the Client/Brand File if desired.
Using Google to search NEOSYS wikis
Mediawiki's built in search is nowhere near as smart as Google's but Googles search often lists non-NEOSYS pages.
Search like this:
neosys wiki "exchange rate"
Putting Exchange Rate in "" quotes searches for the exact phrase instead anywhere either word appears